Last Updated on: 5th December 2023, 04:45 pm
Web site: browser.redcore.cn
Category: Network
Subcategory: Web browsers
Platform: Android, iOS, Linux, Windows
License: Freeware
Interface: GUI
First release: August 3, 2018
Redcore Browser – a Chromium based web browser created by Chinese company Redcore Times (Beijing) Technology Ltd.
Features:
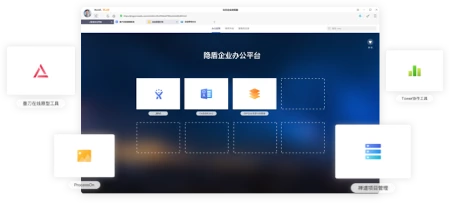
– Hidden Shield Stealth Defense System is a browser-based security access program. Hidden Shield Stealth Defense System focuses on the usage scenarios of external personnel accessing the intranet, which is simpler and safer than VPN. Incognito S includes three components: enterprise browser, incognito gateway, and control background
– SDP is a mature security model. The Cloud Security Alliance has organized 4 SDP hacking contests, and no one has breached it so far. Gartner predicts that SDP will quickly become popular in 2018, and by 2021, 60% of enterprises will use SDP solutions to replace VPNs.
– Private DNS – The administrator can not perform DNS resolution on the external network, but only set the correspondence between the domain name and IP of the business system in the management and control background. When the user logs in to the browser, he obtains the IP of the business system from the background, and then accesses the business system. Because the DNS and IP of the business system are not exposed on the Internet, hackers cannot initiate network attacks.
– Dynamic firewall – Incognito incognito gateway “rejects all” connections by default, and will only receive the first packet with identity information sent by the corporate browser. After the server is authenticated, the browser will be allowed to establish a connection. Hackers cannot see the open ports and cannot scan the server. Moreover, hackers cannot see the content of the server, so they cannot see the value of hacking the server, which reduces the hacker’s willingness to attack.
– Application level access – Hidden Shield SDP only allows application-level access and does not expose the intranet. Even if malware is installed on employees’ computers, they cannot scan and steal resources on the intranet.
– On-demand authorization – The administrator can reasonably restrict which applications users can access in the background. For example, only employees in the finance department are allowed to access the financial system, but not the HR system. Unauthorized access will be blocked by the gateway. In this way, over-authorization of users is avoided, the attack surface is greatly reduced, and the possibility of employee leaks is also reduced.